Cybersquatting is the act of registering a domain name which looks similar to a target domain in order to perform malicious activity. This includes facilitating phishing campaigns, attacking genuine visitors who mistyped an address, or damaging a brand’s reputation. This article will cover the dangers of cybersquatting, what companies can do about it, and outline a plan for a tool which can be used to detect potentially malicious domains.
Many phishing campaigns use generic domains such as discountoffers.com which can be used against any company under the guise of offering discounts or money back. This can then be expanded to use a subdomain such as acme.discountoffers.com to more precisely target a specific brand. However, other more targeted campaigns will use names similar to a legitimate one owned by the target in the hopes that a victim either won’t notice the misspelling or think that the domain is genuine. A real-world example of this was the case of Air France who own www.airfrance.com, as a cybersquatter registered www.arifrance.com and www.airfranceairlines.com to divert users to a website selling discount travel deals.
Companies spend huge amounts of money registering domains that are similar to their primary ones in an attempt to prevent them potentially being used maliciously in the future. Due to cost and logistics, it’s impossible to register every possible domain an attacker might take advantage of, and often by the time a company considers taking such a step, some domains have already been registered. In this latter case, as it’s too late for the company to register it themselves, the next best thing is to be aware of them so action can be taken accordingly.
Common Cybersquatting Techniques
There are several routes an attacker may take in order to choose a domain which is likely to be successful against their target. The following sections detail a few of the thought processes an attacker might go through when choosing a domain using “google.com” as the sample target.
Misspelling
This is when a cybercriminal registers a misspelled domain, and is often known as typosquatting. These types of domains would be where the attacker is hoping a user will accidentally type the target name wrong. Some of these would be based on substituting letters for ones which are next to it on the keyboard or characters typed in a slightly different order. Examples include:
- googel.com
- gogle.com
- soogle.com
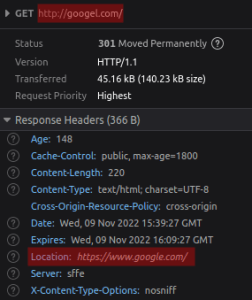
As shown below, Google has proactively registered some domains to protect their users and their trademark, redirecting them to the genuine website.
Similar looking
These are URLs which look similar to the target and although they could be mistyped by a user looking to visit the target domain, they could also be ones designed to not be typed by the victim. For example, to be used as a link in a phishing email where the attacker hopes the victim doesn’t notice due to its similarity. Techniques for this could include replacing letters with numbers, “i” with “L”, swapping letters around, etc. Examples include:
- g00gle.com
- googie.com
- gooogle.com
Legitimate looking
Another potential technique is registering domains which don’t contain typos and aren’t designed to look like the target but a victim might think it genuine. This could include registering different top-level domains using the legitimate company name, or prepending/appending words to the target. Examples include:
- googlesupport.com
- google.net
- google-discounts.com
What can I do if someone registers my domain?
So you have identified a list of similar domains to yours. You’ve investigated and found that one of the domains has mirrored your own website and is being used to launch phishing campaigns against your employees. What do you do now?
In the United States there are two avenues for legal action:
- Internet Corporation of Assigned Names and Numbers (ICANN)
- Anticybersquatting Consumer Protection Act (ACPA)
ICANN Procedure
ICANN has developed the Uniform Domain Name Dispute Resolution Policy (UDNDRP), to resolve disputes for domains which may potentially infringe on trademark claims. A person can bring an action by complaining that:
- A domain name is identical or confusingly similar to a trademark or service mark in which the complainant has rights; and
- The domain has no rights or legitimate interests in respect of the domain name; and
- The domain name has been registered and is being used in bad faith.
If the action is successful, the domain will either be cancelled or transferred to you.
Legal Action Under the ACPA
The Anticybersquatting Consumer Protection Act (ACPA) was enacted in 1999 in order to combat cybersquatting such as the case described in this article. A trademark owner may bring an action against a squatter who:
- Has a bad faith intent to profit from the trademark
- Registers, traffics in, or uses a domain name that is
- Identical or confusingly similar to a distinctive trademark
- Identical or confusingly similar to or dilutive of a famous trademark
- Is a protected trademark
A UDNDRP proceeding is generally the more advised course of action to take, as they tend to be faster and cheaper.
User awareness and technical solutions
As these proceedings can be time consuming (or if your business is based outside of the United States), more immediate measures can be taken to at least protect a client’s own internal users. Making employees aware of a new phishing site is one of the quickest and easiest steps that can be taken to help them stay on the lookout and reduce the chance of success for the attacker.
In addition to this, email policies can be set up to block incoming emails from these potential phishing domains so that they never reach employees in the first place. Some determined attackers may attempt to get round this by contacting employees via another medium such as telephone, coercing victims to visit their site manually via a web browser. In these cases, networking solutions may be able to help to prevent users from connecting to these malicious domains at all by blocking them at the firewall level.
Conclusion
Cybersquatting is threat which is often overlooked, and many companies either don’t consider protection until they’ve been affected by it, or believe it’s something they aren’t able to proactively defend against. Nettitude are aiming to assist clients further in this area by developing the tools to allow domains to be continuously monitored for potentially suspicious permutations.
 Worldwide (English)
Worldwide (English) Romania (Romanian)
Romania (Romanian) Spain (Spanish)
Spain (Spanish) Germany (German)
Germany (German) France (French)
France (French) Bulgaria (Bulgarian)
Bulgaria (Bulgarian) Indonesia (Indonesian)
Indonesia (Indonesian) Portugal (Portuguese)
Portugal (Portuguese) South Africa (Zulu)
South Africa (Zulu)